Fuzz Testing
An Effective Technique for Detecting Unknown Vulnerabilities
In this increasingly connected world, security testing has become an essential part of the development process. Fuzz testing has proven to be an effective technique for detecting unidentified security-relevant faults (0-day vulnerabilities). Using fuzzing, the interfaces of the system under test are faced with invalid and unexpected inputs in a variety of ways in order to test their robustness.
Random fuzzing is the easiest way to find vulnerabilities. However, due to the complexity of the input space, it does not offer a sufficient level of efficiency to test the system comprehensively. Smart fuzzing uses models of your interfaces, protocols or services to generate test cases and thus, reducing the large number of test cases to only the most relevant ones and allowing complex errors to be discovered. Smart fuzzing is therefore considerably more efficient when compared with random fuzzing techniques.
We develop fuzzing heuristics both for data fuzzing (based on Fuzzino) as well as for behavioral fuzzing, tailored specifically to your interfaces, protocols and services. We employ and reuse functional test models taking advantage of an existing model-based testing process. However, even if functional test models are not available, we start with functional test cases or system traces and thus, reduce the initial barriers. By using additional information from a risk analysis, the test process becomes considerably more efficient.
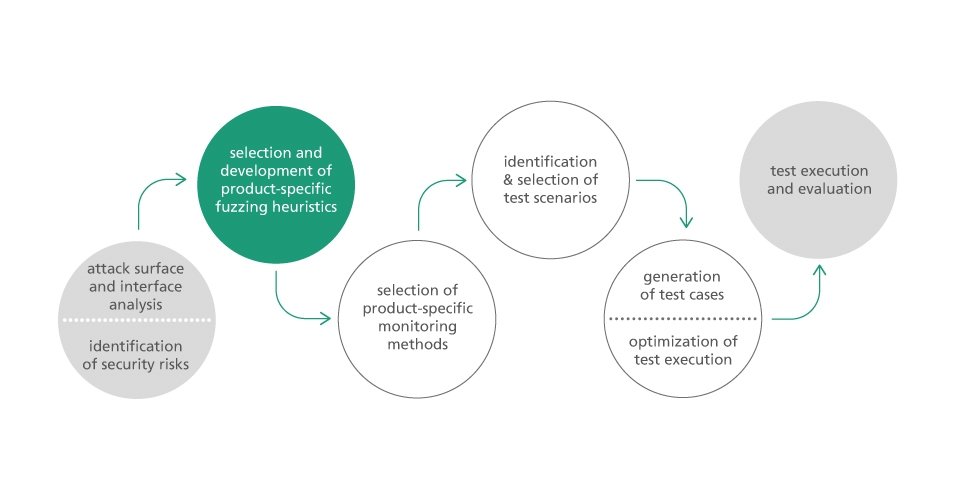
Our process is based on an analysis of the system under test as well as on a risk analysis, if available. On the basis of these results, custom-tailored fuzzing heuristics will be chosen and new ones will be developed. The next step is selecting and annotating suitable test scenarios. Security and robustness test cases are automatically generated from these scenarios. Using the example of an industrial partner's banknote processing system, we have created a risk analysis together with system experts. Afterwards, we examined its protocol for possible weaknesses with the help of functional test cases. Based on these functional test cases and with the help of the risk analysis, suitable functional test cases were chosen and specific security tests are generated. Both data and behavioral fuzzing were applied for this purpose. Thanks to an optimized runtime environment, a high coverage of risks could therefore be achieved in a reasonable amount of time. Results can be found on the website of the several awards winning DIAMONDS project.
Fuzzino, our basic solution for fuzzing, has already been used by various tool suppliers, including Dornier Consulting in its tool do.ATOMS for model-based testing, and Spirent’s TTworkbench, a TTCN-3-based test automation platform. With the help of Fuzzino, both security tests and functional tests can be carried out using the very same tool and enables reusing functional test cases for security testing.
Services
- Analysis of product-specific interfaces, protocols, and services and development of custom-tailored fuzzing heuristics
- Preparation and implementation of security and robustness tests for your product using fuzzing
- Support with implementing fuzz testing into your test process and integrating Fuzzino into your test tools
- Cybersecurity risk analysis as a basis for an efficient risk-based security testing process